Considering software development outsourcing? Explore the importance of security and compliance in this insightful blog. Discover strategies for vendor assessment, defining security requirements, and implementing secure coding practices. Learn how regular audits, data protection measures, contractual agreements, and continuous monitoring contribute to a secure outsourcing process.


In the ever-evolving landscape of technology, companies increasingly turn to software development outsourcing to harness external expertise, streamline costs, and improve project timelines. Among the outsourcing models, nearshore outsourcing has gained popularity for its geographic proximity, enabling better collaboration and communication. As organizations embark on this collaborative journey, a critical aspect that demands intense attention is the handling of security and compliance. In the interconnected world of software development, where sensitive data flows across borders, ensuring the safeguarding of information and maintaining regulatory standards becomes paramount. This blog explores the importance of handling security and compliance in software development outsourcing, shedding light on why it is not just a priority but an essential requirement for companies navigating the outsourcing concept.
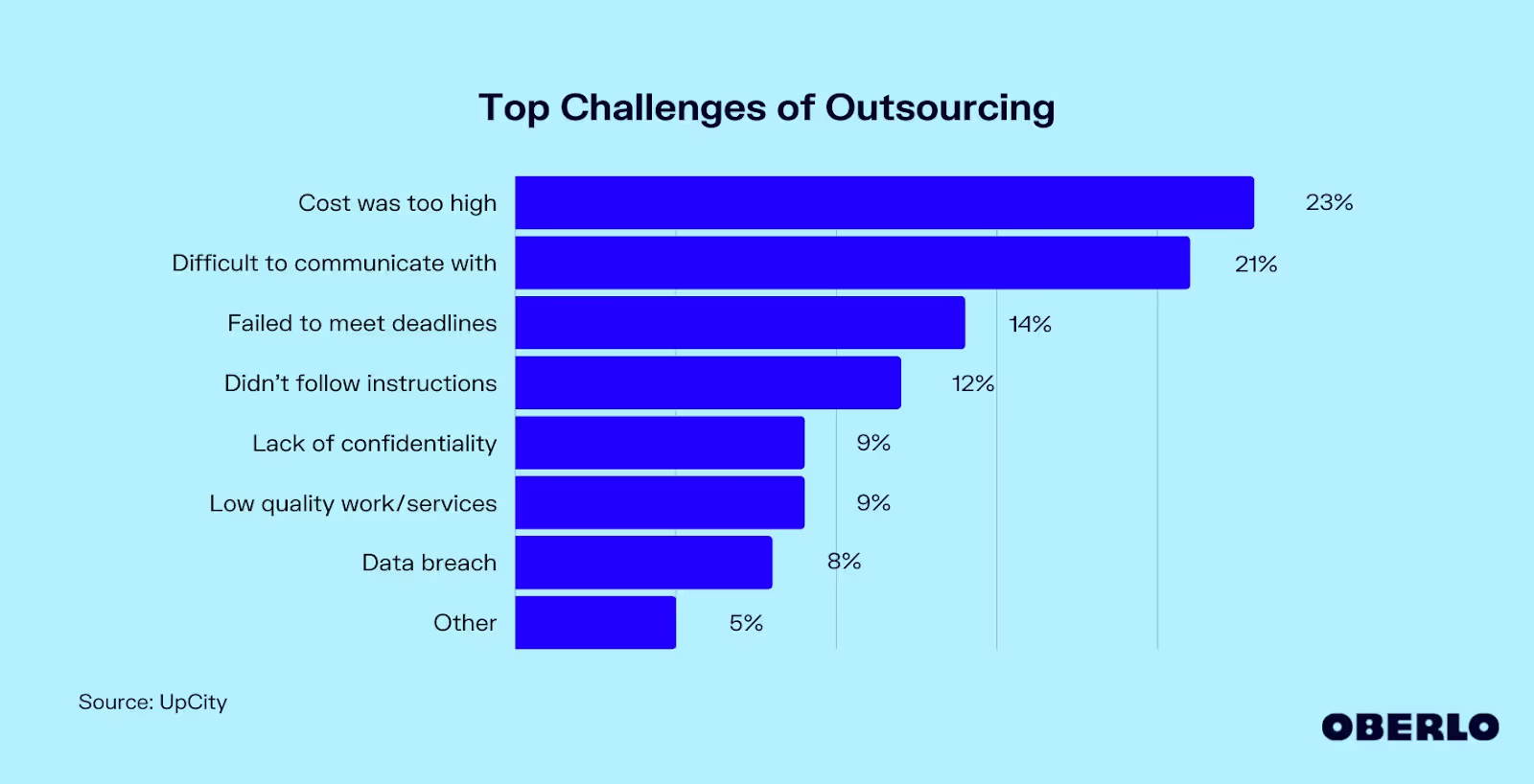
As you can see from the above statistics, security issues are one of the top most challenges that employers when outsourcing. In this section, we carefully discuss the best strategies that can help you maintain outsourcing security whenever you opt for software development outsourcing or nearshore staff augmentation.
When you're thinking about outsourcing your software development, the first step is to check out the potential partners. Take the time to look at their history—what projects they've done before and what other clients are saying about them. You want a team that has a good reputation for prioritizing security and playing by the rules. Consider their skills, the way they work, and if they stick to the standards that everyone in the industry agrees on.
Before you hand over your project to an external team, make sure everyone is on the same page about security. Clearly explain your expectations to the outsourcing team. Provide them with detailed documents outlining the specific security measures and compliance standards you want them to follow. This way, everyone is clear on what needs to be done to keep the project safe and in line with the rules.
You want the code for your software to be as secure as possible. Encourage the development team to use guidelines that prioritize security. Make sure they receive training on the best practices for creating code that keeps things safe. This includes things like checking the input, encrypting data, and using secure authentication methods. Regularly remind the team about the importance of writing code with security in mind throughout the development process.
Don't wait until the end to check if your software is secure. Schedule regular security audits and testing throughout the development process. Conduct penetration testing and code reviews to identify and address potential vulnerabilities. Use automated testing tools to perform routine security checks. This proactive approach helps catch and fix security issues early in the development cycle, reducing the chances of vulnerabilities making it into the final product.
Take extra care to protect sensitive data and respect user privacy. Clearly define policies for handling data and make sure they comply with relevant data protection regulations. Implement encryption for data both in transit and at rest. Regularly audit access controls to prevent unauthorized access to sensitive information. It's crucial that the outsourcing team understands and adheres to your organization's policies regarding data protection.
When working with an external team, it's essential to have clear agreements in place. Draft comprehensive contracts that include specific clauses about security and compliance. Clearly outline the roles and responsibilities related to security measures. Include Service Level Agreements (SLAs) that detail performance expectations and consequences for security breaches. These legal documents serve as a foundation for ensuring that security and compliance requirements are met throughout the entire outsourcing engagement.
Establish a system for continuous monitoring of security and compliance measures. Regularly review and update security protocols to align with evolving threats and industry standards. Encourage a culture of continuous improvement, where the outsourcing team actively learns from incidents, implements corrective actions, and stays informed about emerging security trends. This ongoing vigilance ensures that security remains a shared priority throughout the software development process.
Maintain open and transparent communication channels with the outsourcing team, fostering a collaborative environment where concerns related to security and compliance can be raised and addressed promptly. Set up a feedback loop that allows both parties to share insights and improvements, creating a dynamic communication flow that not only expedites issue resolution but also strengthens the overall partnership. Regular and proactive communication becomes the backbone of a robust collaboration, ensuring that security remains a shared focus throughout the software development process.
Incident Response Planning is a critical component of security measures in software development outsourcing. Collaborating closely with the outsourcing team, it is imperative to develop a robust incident response plan that clearly outlines the necessary steps to be taken in the unfortunate event of a security incident or compliance breach. In addition to this, ensuring that all team members are not only aware but also well-versed in the plan is essential. Regular drills should be conducted to test the plan's effectiveness, ensuring a proactive and coordinated response. A well-prepared incident response plan proves instrumental in minimizing the impact of security incidents, fostering resilience, and facilitating a swift, organized response when the need arises.
Document all security and compliance procedures and provide comprehensive training to the outsourcing team. Ensure that team members understand the importance of adhering to security measures and compliance standards. Regularly update training materials to incorporate new insights and industry developments. This investment in education helps create a security-conscious development team and contributes to a safer software development outsourcing process.
At Blue Coding, we bring talented developers from Latin America to help you with your projects. Our team includes IT consultants who are ready to guide you every step of the way. We understand how important your ideas and data are, so we make sure to keep them secure. Your intellectual property and information are our top priority. If you're ready to explore the benefits of outsourcing with us, contact us today to get started!
Subscribe to our blog and get the latest articles, insights, and industry updates delivered straight to your inbox